🚦🔴📜CA - Block Authentication Transfer
What this policy is for
This Conditional Access policy blocks Authentication Transfer for all users — except those who genuinely need it.
Authentication Transfer is a feature that lets users pass their authentication context from one device to another, creating a security gap if not controlled.
While it sounds convenient, it can also become a backdoor if misused. This policy ensures that only explicitly allowed users can leverage it, while everyone else gets blocked by default.
Used in combination with:
🔐 Configuration Overview
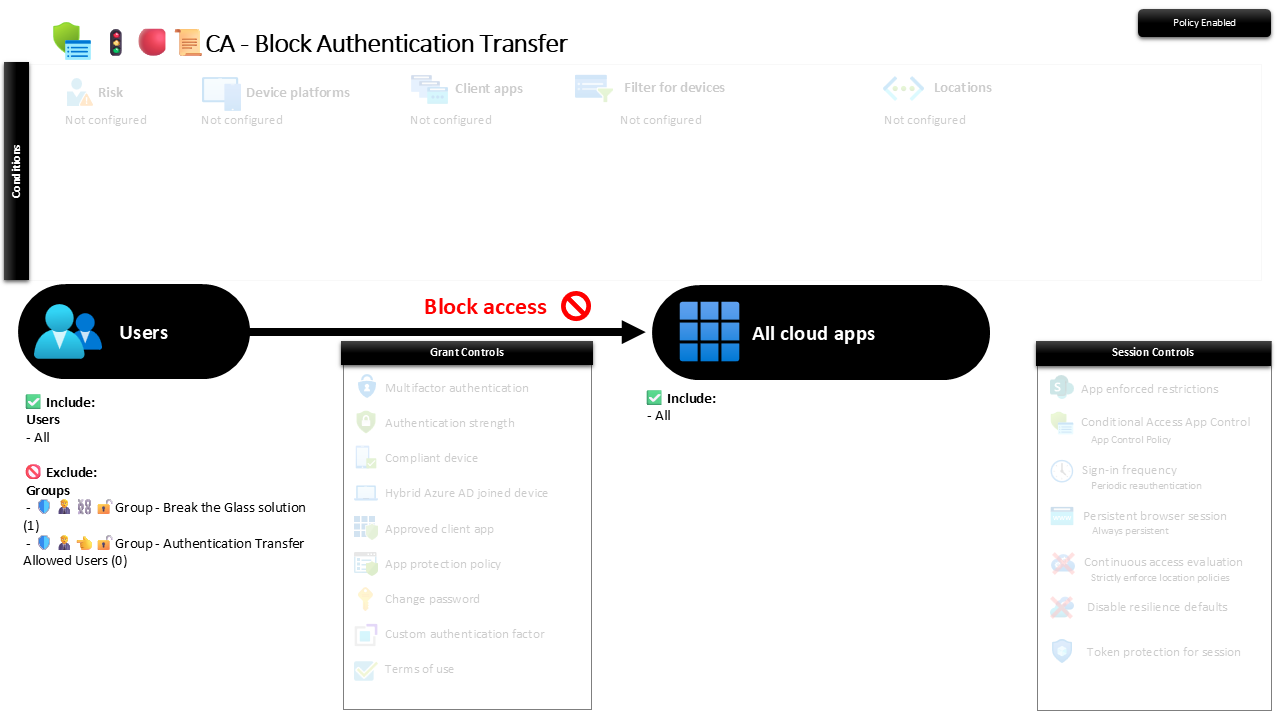
📌 Purpose and Impact
This policy creates a controlled environment where:
- All users are blocked from using Authentication Transfer by default
- Only users in the exclusion group can transfer authentication sessions
- Break-the-Glass accounts are excluded to prevent emergency lockouts
Why this matters:
- Prevents unauthorized authentication context sharing between devices
- Reduces lateral movement opportunities for attackers
- Maintains visibility over who can transfer authentication sessions
- Keeps authentication sessions tied to the original device unless explicitly allowed
🎯 "Authentication Transfer is like handing someone your car keys — convenient, but only do it with people you trust."
🧭 Governance & Security
Authentication Transfer should be treated as a privilege, not a right:
- Regularly review the Authentication Transfer Allowed Users group
- Only grant access to users with legitimate business needs
- Monitor authentication transfer events in sign-in logs
- Document why specific users or roles need this capability
- Remove access when it's no longer needed
Best practices:
- Start with zero users in the allowed group
- Add users based on documented requests only
- Set up alerts for authentication transfer attempts by blocked users
- Review the exclusion group quarterly
🔐 "If you can't explain why a user needs Authentication Transfer, they probably don't."
🧠 Final Note
Authentication Transfer is powerful, but power requires control.
This policy ensures that convenience doesn't compromise security.
Block by default. Allow by exception. Monitor everything.
🚫 "Your authentication is yours — don't let it wander off without permission."