🚦🔴👨💼CA - Block Remote Work for not allowed users
What this policy is for 🧭
Some roles are office-only — by design.
This policy makes sure those users can only sign in from your trusted, on-site networks (your customer locations).
Anywhere else? Blocked.
In short: members of the Not Allowed to Work Remote group can work at HQ only — not from cafés, home Wi-Fi, or “mysterious” IPs on the internet.
Combined with 🧩
Together, they create a clean rule:
If you’re in the group and you’re not at a Customer Location → access is blocked.
🔐 Configuration Overview
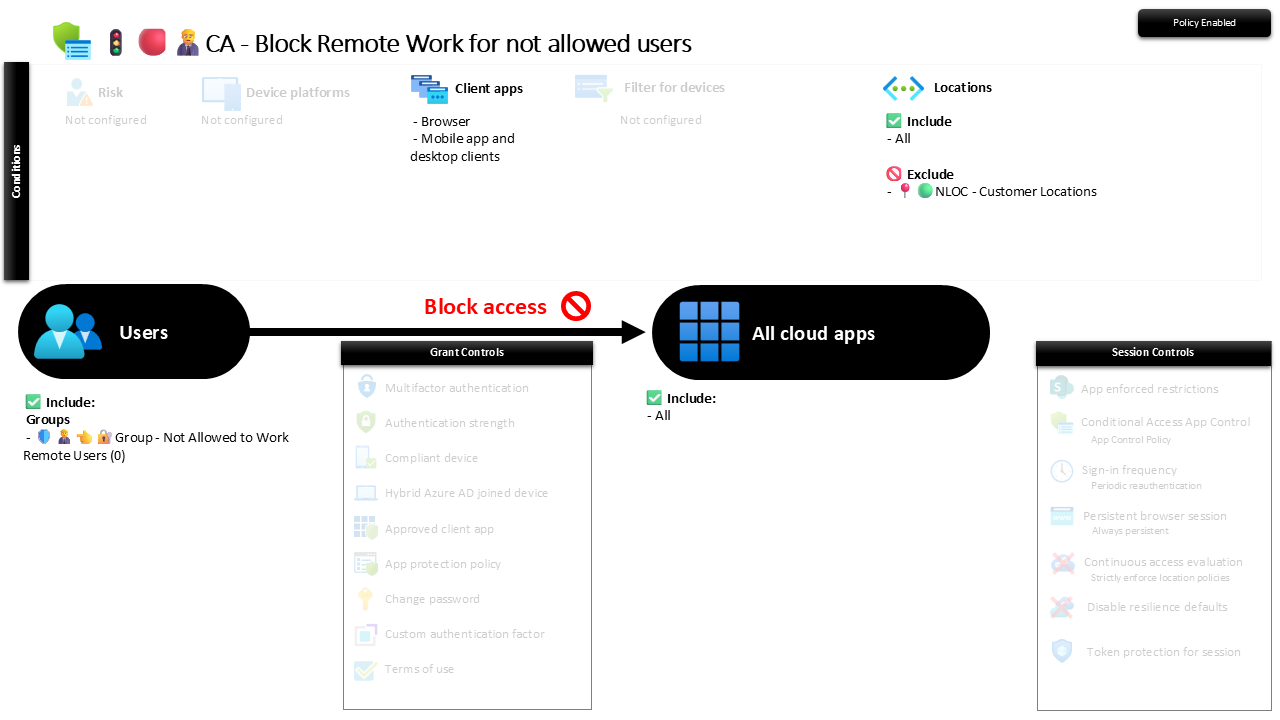
How it works:
- Users in the group can authenticate only when the sign-in originates from a defined Customer Location (your trusted IP ranges).
- From any other location, sign-in is blocked across all apps.
📌 Purpose and Impact
This policy enforces predictable access for office-bound roles:
- Reduces risk from unmanaged and unknown networks
- Keeps compliance tight for roles that must remain on-prem
- Cuts down incident noise from “random” remote sign-in attempts
It’s simple, auditable, and easy to reason about: office-only means office-only.
🧭 Governance & Security
Before rollout:
- Align with HR/management on which roles are office-only
- Populate 🛡️🧑💼👈🔐Group - Not Allowed to Work Remote Users accordingly
- Validate 📍🟢NLOC - Customer Locations (IPs, VPN egress, branches)
After rollout:
- Review group membership regularly (joiners/movers/leavers)
- Monitor blocked sign-ins — repeated hits can indicate compromised credentials
- Re-verify named location ranges after WAN/VPN changes
🛑 “Remote access isn’t a right — it’s a scoped exception.”
🧠 Final Note
This is your on-site only guardrail.
Keep the group tight, keep the locations accurate, and you’ll keep risk — and noise — way down.
Set it. Test it.
And let the perimeter do its job. 🌐🔒